Our JavaScript Obfuscator Pro 2025 transforms your readable JavaScript code into a protected, highly secure version that maintains full functionality while being extremely difficult for hackers to reverse engineer. Unlike basic minifiers, our tool employs advanced techniques like control flow flattening, dead code injection, and string encryption to provide maximum security for your intellectual property.
What Makes Our JavaScript Obfuscator Different
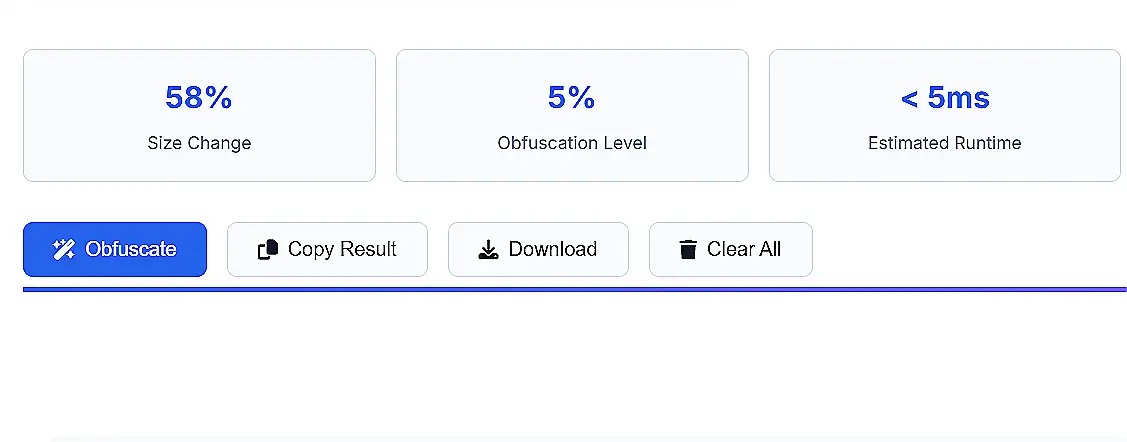
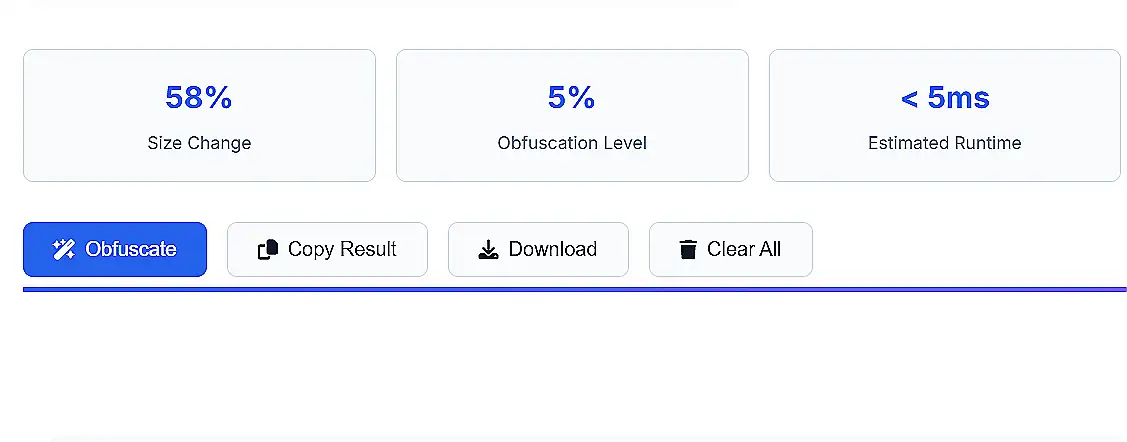
Unlike simple minifiers that only remove whitespace and comments, JavaScript Obfuscator Pro 2025 applies sophisticated transformations to your code that make it virtually impossible to reverse engineer while maintaining 100% functionality.
Protect Your Valuable Code Assets
Whether you're developing premium WordPress plugins, JavaScript libraries, SaaS applications, or proprietary algorithms, our obfuscator helps ensure your competitive advantage stays protected from theft and unauthorized use.
Try JavaScript Obfuscator Pro 2025 Today
Start protecting your JavaScript code with our advanced obfuscation tool. No registration required to try basic features.